Digital Organisation samenvatting
2017-2018
De cursusdienst van de faculteit Toegepaste
Economische Wetenschappen aan de Universiteit
Antwerpen.
Op het Weduc forum vind je een groot aanbod van samenvattingen,
examenvragen, voorbeeldexamens en veel meer, bijgehouden door je
medestudenten.
Digital Organisation
Introduction
Vision of Europe European Commission: digital future of Europe à Digital transformation is a global element (Better in Asia and America, we have to keep with up with their digital transformation) We have to invest more, but we also need the proper kills to put these technologies to effective use (= e-skilled)Chapter 1: Information Systems In Business Today
Rugby Football Union Tries Big Data • Objective of the Union – Promote Rugby Not typically associated with digital organisations, the main activity is playing rugby or football • Problem – Improving fan engagement through Big Data. • Solutions – Provide data visualization and real-time statistics to draw in fans. – Provide tactical insights to players and coaches that will improve match play. • Rugby Football Union uses Try Tracker to capture and analyse Big Data that will be useful to both fans and players. • Demonstrates IT’s role in increasing value and revenue in any business. • Illustrates the potential for technology to improve customer experience. - Modern football teams are highly levering technology to improve their business model - Mobile phone to order food or a drink when you’re sitting in your seat at the game - Increase the experience ands the satisfaction from the audience = high tec The only interest to increase the experience of the audience is to increase sales, with the help of new technologies How Information Systems Are Transforming Business Over the past 2 decades the amount of capital investments has been growing – It is not business as usual anymore in the global economy. Information systems are transforming our economy. – Increasing investments in IT (see next slide) § Mobile digital platform For example: the banking sector, businesses like amazon.com & bol.com § Systems used to improve customer experience, respond to customer demand, reduce inventories, and more § Growing online newspaper readership § Expanding e-commerce and Internet advertising § New federal security and accounting laws When new business models emerge: laws ands regulations are impacted because the current law is not really accommodating – As a manager, you want to make sure you make the right investments. Key question: are you capable as a manager to make the right investments? Figure 1.1: Information Technology Capital InvestmentWhat’s New in Management Information Systems Digital transformation is going at a very fast pace: each time new technologies pop up we have to review our current business strategies • Plenty new things, makes this area very exciting! Some important ones: • New Technology Innovations – Cloud computing Store your data in the cloud: Pinterest does it: they do it in the context of their business Risk? Example: data of a hospital was leaked on the internet. Businesses do this because of the cost reduction but there is a risk Salefore.com: a whole business in the cloud – Big data and the Internet of Things (IoT) Like a smart city: chip in garbage bin, only go to bin that’s full Everything starts to talk to everything, highly impact the business technologies: even inventing new things Like Uber who fully turned down the services of a taxi, they used technology for this – Mobile digital platform • New business models (eg. Uber etc) • Expanding e-commerce • Management changes – Online collaboration and social networking software – Business intelligence – Virtual meetings Impacting the way we work together (Blackboard, google docks) • Changes in firms & organizations More and more parts of IT are currently outsourced ‘’It doesn’t matter’’ – Carr 2003 (!) Parallel between IT and electricity namely the first companies who started with electricity had a huge advantage = unique But what happened to the electricity as an asset? It has become a commodity: we try to use it at a low cost: same is happening to IT There is a part in IT that has commodities: examples: laptop, iPhone, printer (outsource this kind of IT) ‘’Business processes do matter’’ – Carr Business technologies can really impact the businesses, for an example as bol.com IT does matter Globalization Challenges and Opportunities: A Flattened World • Internet has drastically reduced costs of operating on global scale • Presents both challenges and opportunities – Increases in foreign trade, outsourcing Different societies are doing business with each other: the world has become flat again: the internet brought a huge leverage in the globalization of the world à Business have to keep reinventing themselves, so they can create a good society Globalizations has pro’s and con’s Pro’s: we are able to do in a much easier way business around the globe, our market has extended Con’s: a lot of industries are leaving Europe and build businesses in China and India, outsourcing has become much easier
The Emerging Digital Firm • In a fully digital firm: – Core business processes are accomplished through digital systems (logistics) – Key corporate assets are managed digitally (eg. HR, finance) – Significant business relationships are digitally enabled and mediated • Digital firms offer greater flexibility in organization and management – Time shifting, space shifting = do business in a virtual market (online shopping) = work 24 hours on 24 hours Strategic Business Objectives of Information Systems • Growing interdependence between: – Ability to use information technology and – Ability to implement corporate strategies and achieve corporate goals • Firms invest heavily in information systems to achieve six strategic business objectives: 1. Operational excellence Understand how your business process is operated and making it as cost efficient and effective as possible The fulfilment tac: when someone orders a package it requires a lot of technology to get it in time by the customer Retail: fully automated supply chain: how much milk is still available in the store and do we have to supply more now? 2. New products, services, and business models iTunes has turned the music industry down (highly impacted) you can now legally stream music à It is no longer physical (CD) Uber: taxi industry Air bnb: hotel industry 3. Customer and supplier intimacy Hotel chains who try to capture your data and preferences, they will make sure that in your room your favourite song is playing and the temperature is exact what you like: fully automated KLM: flying with airplanes has become a commodity, you chose your flight based on the price. It is important to increase customer satisfaction à KLM Invested a lot in social media, when u lose your baggage you can put your complaint on Facebook or twitter and KLM guarantees that within one hour you are contacted with a solution = creating a unique facility, considering this when choosing a flight 4. Improved decision making A chain of bakers: educate the bakers so that they are up to date with the health regulations Bakery battle app: game on health regulations, security regulations à Bakers that had a bad score put together with bakers that had a good score so they could work together and learn from each other à Managers are able to quickly review an employee
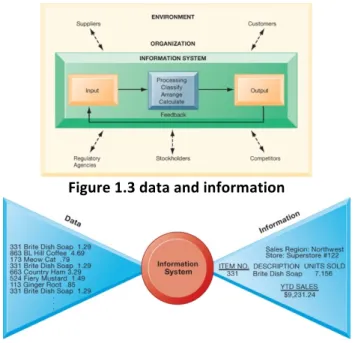
5. Competitive advantage Continuously improving experience: to be competitive: have an advantage First bank à internet à All the banks become internet bank à First bank à Mobile bank à All the banks become mobile banks Very competitive industry: what is going to happen next? 6. Survival Firms have to keep up with other companies in order to be competitive: invest in information systems and technology: necessities of doing business GDPR General data production regulations: all companies in Europe have to ensure that all personal information is guarantied to be confidential and integrated: require an investment in IT, can get a fine if they don’t invest and don’t keep up with this regulation Sox CEO/CFO has to guarantee in person that all the facts in the financial report are accurate and correct if it’s not accurate the fine is not a fine on the revenue but the CEO/CFO goes to jail à Technology helps to keep it accurate and keeps it protected so other people don’t have access Video Case: https://www.youtube.com/watch?v=oBOeWylSMfM Which of the six reasons to invest in it did we come across in this video? − Operational excellence Moving packages is a commodity activity, making their supply chain as operational excellent as possible − Competitive advantage: claim to be the best in this supply chain − Survival − Customer intimacy You can see where your package is, even when it is too late − Improves decisions making Weather forecast to improve way they use airplanes What Is an Information System? • Information system – Set of interrelated components – Collect, process, store, and distribute information – Support decision making, coordination, and control Capture data (input) and arrange the data so it results in information (output) Collection of activities that collect processes and delivers information to the audience • Information vs. data – Data are streams of raw facts – Information is data shaped into meaningful form If you go to the store and you buy stuff and you get a ticket, left side of the ticket are data elements (beer, milk) when does it become information? ‘Colruyt has sold 10 bottles of milk’ à Data has become aggregated
Figure 1.3 data and information Dimensions of Information Systems: Organizations Different layers of the organization, requirements of the information systems are different from layer to layer • Hierarchy of authority, responsibility – Senior management Long-range strategic decisions about products and services: ensure financial performance of the firm – Middle management Carries out the plans of the senior management – Operational management Monitoring the daily activities of the business – Knowledge workers Design products or services: create new knowledge for the firm – Data workers Assists with communications at all levels of the firm – Production or service workers Produce the product: deliver the service • Separation of business functions – Sales and marketing – Human resources – Finance and accounting – Manufacturing and production • Unique business processes • Unique business culture • Organizational politics Dimensions of Information Systems: Management How are information systems delivering value? Information systems capture data, transform data into information, give information to business processes and management activities • Managers set organizational strategy for responding to business challenges • In addition, managers must act creatively – Creation of new products and services – Occasionally re-creating the organization
Change their business strategies to the disruptive technology • Computer hardware and software • Data management technology • Networking and telecommunications technology – Networks, the Internet, intranets and extranets, World Wide Web • IT infrastructure: provides platform that system is built on Figure 1.7: The Business Information Value Chain It Isn’t Just Technology: A Business Perspective on Information Systems • Investing in information technology does not guarantee good returns • There is considerable variation in the returns firms receive from systems investments • Factors – Adopting the right business model – Investing in complementary assets (organizational and management capital) There is much more to be done than just investing in IT à Value Assumptions: if you invest in IT the value will go up = no correlation = IT black hole = we invest in IT but we don’t see the benefits in value When will the benefits emerge? When the sales and the marketing people start to use the working system Getting value out of information systems requires investment in IT + much more investment in changing behaviour, changing your business policy, educating your people… Figure 1.8: Variation in Returns on Information Technology Complementary Assets: Organizational Capital and the Right Business Model – Assets required to derive value from a primary investment – Firms supporting technology investments with investment in complementary assets receive superior returns – Example: Invest in technology and the people to make it work properly – Complementary assets – Examples of organizational assets – Appropriate business model
– Efficient business processes – Examples of managerial assets – Incentives for management innovation – Teamwork and collaborative work environments – Examples of social assets – The Internet and telecommunications infrastructure – Technology standards Academic disciplines involved Bringing many different academic disciplines into management information systems = very multidisciplinary course à Technical and behavioural approaches Bringing together 2 eras: boundary between business and IT Figure 1.10: A Sociotechnical Perspective on Information Systems
Chapter 2:
Global E-business and Collaboration
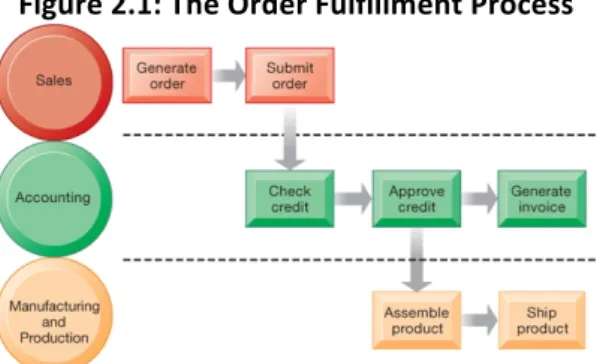
What are the business processes in an organization? What is the role of information system depending on where u are in the organisation? More specific: collaboration and social business Enterprise Social Networking Helps ABB innovate and Grow • Problem – Outdated static technology – Geographically dispersed • Solutions – Develop knowledge sharing strategy and goals – Change knowledge and collaboration processes – Change organizational culture – Deploy Inside+, with Yammer, Office 365, and SharePoint • ABB uses Inside+ to provide new channels for knowledge acquisition, innovation, and collaboration • Demonstrates IT’s role in helping organizations improve performance and remain competitive • Illustrates the ability of IT systems to support collaboration and teamwork Building and selling power generators: widespread in the world: information system supporting the business is rather complicated: if someone wants information of the organisation he has to log into 7 different systems Organisations who are moving from a situation where they have to log into 7 systems to a 1 integrated system for the whole business à this can highly increase the efficiency Business Processes • Business processes – Flows of material, information, knowledge – Sets of activities, steps – May be tied to functional area or be cross-functional A set of activities that together transform information into a specific service or value for the customer • Businesses: can be seen as collection of business processes • Business processes may be assets or liabilities Liability: the way they operate the sales and marketing way is not being done good The business as a whole can never have a view on everything because the working people are sometimes keeping information behind Asset: doing sales and marketing process very good • Examples of functional business processes – Manufacturing and production • Assembling the product – Sales and marketing • Identifying customers – Finance and accounting • Creating financial statements – Human resources • Hiring employeesFigure 2.1: The Order Fulfillment Process How Information Technology Improves Business Processes • Increasing efficiency of existing processes – Automating steps that were manual • Enabling entirely new processes – Changing flow of information – Replacing sequential steps with parallel steps – Eliminating delays in decision making – Supporting new business models Technology can make sure that the business process is run in a more efficient way Use technology to really rethink the way we are doing business: highly automate a business process to increase efficiency For example: − Tax office: every year people have to submit their salaries. In the past it was a paper based process. Now they automated the process: fill in the income statement online and in the tax office it was printed out: back to paper bases: little bit different − If you are retired it means that u receive a pension from the government: fill in what you got from the government. Now government has integrated their data bases: now they send u a tax claim with already all the data they have from you and they just have to click on ‘’I agree with the statement’’ = rethinking the process Systems for Different Management Groups • Transaction processing systems Systems that typically automate recurring operational activities in business processes – Serve operational managers and staff – Perform and record daily routine transactions necessary to conduct business § Examples: sales order entry, payroll, shipping, reception in the hotel: complete the information of your booking in the system – Allow managers to monitor status of operations and relations with external environment – Serve predefined, structured goals and decision making • Systems for business intelligence – Data and software tools for organizing and analyzing data – Used to help managers and users make improved decisions • A payroll transaction processing systems à keeps track of money paid to employees It keeps track of money paid to employees: employee data is captured: when are u working at home/when are you abroad: in the past it was paper based • Management information systems For example: this system will report the sales (figure 2.4)
For example: what will happen to our sales when we increase the price with 2%? There is a calculating power in these systems available For example: shipping company (figure 2.5) very different parameters: it will calculate the best route to go from Antwerp to New York • Executive support systems Oriented towards the executive committees/board of an organisation For example: a dashboard, where all different types of information are aggregated into one single overview including external information = non-routine, will help them take appropriate decisions in the organisation Management Information Systems • Serve middle management • Provide reports on firm’s current performance, based on data from TPS • Provide answers to routine questions with predefined procedure for answering them • Typically, have little analytic capability Figure 2.3: How Management Information Systems Obtain Their Data from the Organization’s TPS Figure 2.4: Sample MIS Report
Decision support systems • Serve middle management • Support non-routine decision making – Example: What is the impact on production schedule if December sales doubled? • May use external information as well TPS / MIS data • Model driven DSS – Voyage-estimating systems • Data driven DSS – Intrawest’s marketing analysis systems Figure 2.5: Voyage-Estimating Decision-Support System Executive Support Systems • Support senior management • Address non-routine decisions – Requiring judgment, evaluation, and insight • Incorporate data about external events (e.g., new tax laws or competitors) as well as summarized information from internal MIS and DSS • Example: Digital dashboard with real-time view of firm’s financial performance Enterprise Applications Also information system that brings everything together in one integrated whole • Systems for linking the enterprise • Span functional areas • Execute business processes across the firm • Include all levels of management • Four major applications – Enterprise systems – Supply chain management systems – Customer relationship management systems – Knowledge management systems 2 typologies for looking at information systems
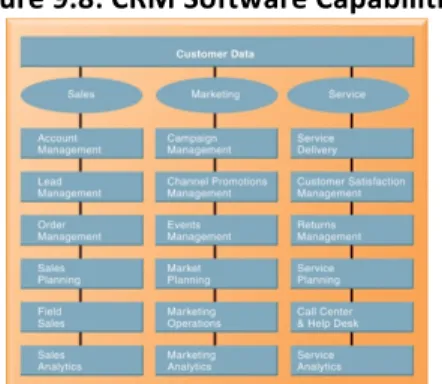
Figure 2.6: Enterprise Application Architecture Enterprise Systems Single central database to store all the information in: all business processes run on one single database: all other elements are integrated à huge advantages: quality of data will be much higher Disadvantage: you have to store your data each time again: inefficient • Collect data from different firm functions and store data in single central data repository • Resolve problems of fragmented data • Enable: – Coordination of daily activities – Efficient response to customer orders (production, inventory) – Decision making by managers about daily operations and longer-term planning – Integration – Standardization Enterprise resource planning ERP à SAP is a brand of an ERP system (most known) SAP has looked at the financial process in many organisations and tried to extract a genetic business process out of it: what is a typical way of doing a typical process, this is stored in those systems: program forces you to use this way of process (standardization): you can put a whole company (Finance, HR, marketing) into a ERP system Supply Chain Management (SCM) Systems Information system that will help u optimise your supplies: system will automatically see what is still in stock and see if your close to having nothing (in a shop for example) • Manage firm’s relationships with suppliers • Share information about: – Orders, production, inventory levels, delivery of products and services • Goal: – Right amount of products to destination with least amount of time and lowest cost – Example: https://www.youtube.com/watch?v=SUe-tSabKag In the system every sold item is tracked: management information system: not only capturing the data but also trying to forecast what u are going to buy Decision support system: external parameters: what is happening to the sales when the weather is bad? Supplier can see the stock of Walmart: he can send stock to Walmart if he sees that they are running out à Example of a supply chain management system
Fulfilment system how can we make sure we fulfil the wishes of the customers? When u buy a product at bol.com/ amazon.com before 11 o’clock your product is shipped at night: get it to your door in less than 24 hours Everything is fully optimised when u click on ‘’buy’’ a robot starts moving: server keeps them from colliding Intern organisational systems Systems that connect two types of business (for example: Walmart and the supplier) Customer Relationship Management (CRM) Systems Business processes: information systems that can help us to better capture the needs of the customers • Provide information to coordinate all of the business processes that deal with customers – Sales – Marketing – Customer service • Helps firms identify, attract, and retain most profitable customers • Example: https://www.youtube.com/watch?v=VYoKsjPiNYA Food service company: try to serve the customer in a personal way: it’s difficult to get new types of customers and when u have them u have to make sure that they stay (attracting them) because of this challenges they us CRM systems In the past: data was not integrated, they didn’t have shared information on the customers Sell, service and market smarter with the world www.salesforce.com Knowledge Management Systems (KMS) All over the place: try to make sure to share knowledge • Support processes for capturing and applying knowledge and expertise – How to create, produce, and deliver products and services • Collect internal knowledge and experience within firm and make it available to employees • Link to external sources of knowledge SharePoint: store and management documents over the organisation: KMS: have a better use and leverage of the information that’s in the organisation Intranets and Extranets • Also used to increase integration and expedite the flow of information • Intranets Mostly only employees who have access to your information – Internal company websites accessible only by employees • Extranets Also customers and suppliers that have access to your information – Company websites accessible externally only to vendors and suppliers – Often used to coordinate supply chain
E-business, E-commerce, and E-government • E-business Systems that are trying to automate our primary and secondary business processes – Use of digital technology and Internet to drive major business processes • E-commerce Using technology to make online market places, buy and selling goods and services to the internet – Subset of e-business – Buying and selling goods and services through Internet • E-government Same as E- business; using technology to innovate the business processes of the government – Using Internet technology to deliver information and services to citizens, employees, and businesses What Is Social Business? Business that are using technology to increase the engagement of employees, customers • Social business – Use of social networking platforms (internal and external) to engage employees, customers, and suppliers • Aims to deepen interactions and expedite information sharing • “Conversations” • Requires information transparency – Driving the exchange of information without intervention from executives or others • Example: https://www.youtube.com/watch?v=H7h4rUBsX3M Global company: people work together in innovation teams: find a way to get groups together in innovation groups while using technology (can’t fly them all over) like an internal social network à how do you create the social place? What’s presented here is very close to the concept of KMS: this type of innovation is close to that: in an easier way share knowledge Challenge: uses social technologies such as wiki, virtual worlds, google dockx Not only about implementing the technologies but also changing the way of operating and collaborating in the organisation (business (people, culture) + technology) Business Benefits of Collaboration and Teamwork • Investments in collaboration technology can bring organization improvements, returning high ROI • Benefits – Productivity – Quality – Innovation – Customer service – Financial performance § Profitability, sales, sales growth Figure 2.7: Requirements for Collaboration
Tools and Technologies for Collaboration and Social Business • E-mail and instant messaging (IM) • Wikis • Virtual worlds • Collaboration and social business platforms – Virtual meeting systems (telepresence) – Cloud collaboration services (Google Drive, Google Docs, etc.) – Microsoft SharePoint and IBM Notes – Enterprise social networking tools Figure 2.8: The Time/Space Collaboration and Social Tool Matrix IT department trying to deliver and implement all the software and applications à Running the IT department is also important The Information Systems Department • Often headed by chief information officer (CIO) – Other senior positions include chief security officer (CSO), chief knowledge officer (CKO), chief privacy officer (CPO), chief data officer (CDO) • Programmers • Systems analysts • Information systems managers • End users CIO (chief information officer) = head of the IT department People who develop (programmers) have to understand the functional requirements and the people who do operations need to make sure the website is running 24/24 and 7/7 Organizing the Information Systems Function • IT governance – Strategies and policies for using IT in the organization – Decision rights – Accountability – Organization of information systems function § Centralized, decentralized, and so on IT governance Decision rules: how do we make appropriate decisions about investing in technology? How can we make sure that our business people and IT people are working well together so we can achieve alignment between business and IT? à Achieve value out of digital transformation: if you design this correctly it’s possible IT governance à alignment à Value
Chapter 3: Information Systems, Organizations, and Strategy
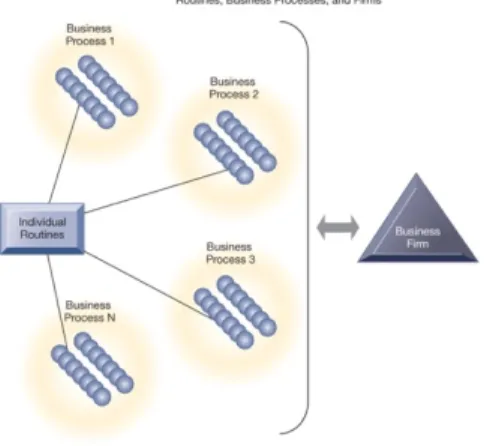
https://www.youtube.com/watch?v=hMa5YHOInIc Old existing organizations, how do they go across digital transformation? The core business is making engines for airplanes. They need to have a lot of smart people and materials in house Engines are full of sensors: when an airplane flies it creates data: help them better understand how engines work à Data science: all industrial space will also be impacted by the digital transformation Tate & Lyle Devise a Global IT Strategy • Sugar production and distribution • Problem – Intense competition – Inefficient manual system of reconciliation • Solutions – Centralize financial accounting at a single location – Bring together all general ledger accounts and transactions into a single system – Integration of legacy systems into the new single system – Revise and simplify business processes based on industry best practices • Tate & Lyle uses technology to produce financial statements with a high degree of accuracy • Demonstrates IT’s role in helping organizations achieve business strategic objectives and remain competitive The Relationship Between Organizations and Information Technology • Information technology and organizations influence each other – Relationship influenced by organization’s § Structure § Business processes § Politics § Culture § Environment § Management decisions What Is an Organization? • Technical definition You have an input, labour and capital, the organisation produces things and in the end you have an output back to the environment We can replace labour by IT (robotics) and then we have another system: can we be more effective and efficient in combining labour and capital? à IT: in practice organizations are not that technical, they are filled with people – Formal social structure that processes resources from environment to produce outputs – A formal legal entity with internal rules and procedures, as well as a social structure• Behavioral definition This element will change the impact of IT on the organization: change peoples culture and beliefs otherwise there will be a resistant: rules, regulations, cultures, norms, values – A collection of rights, privileges, obligations, and responsibilities that is delicately balanced over a period of time through conflict and conflict resolution Figure 3.2: The Technical Microeconomic Definition of the Organization Relation to IT: how are the inputs of labor and capital combined when we introduce technology (or replace labor by technology (robotics)? Figure 3.3: The Behavioral View of Organizations Relation to IT: introducing new IT is more more than just replacing, it might impact rights, value, norms… Features of Organizations Have an impact on how we are going to look at IT • Use of hierarchical structure • Accountability, authority in system of impartial decision making • Adherence to principle of efficiency • Routines and business processes • Organizational politics, culture, environments, and structures Routines and Business Processes People work according to a certain routine: collection of routines will become a business process: all the business processes together form the organizations • Routines (standard operating procedures) – Precise rules, procedures, and practices developed to cope with virtually all expected situations • Business processes: Collections of routines • Business firm: Collection of business processes
Figure 3.4: Routines, Business Processes, and Firms Organizational Politics Politics and power play will always impact our IT decision making: we have to be aware of that. How can u move away from that power play (= attempt to gain an advantage by showing you are more powerful) and make IT decisions more transparent? • Divergent viewpoints lead to political struggle, competition, and conflict. • Political resistance greatly hampers organizational change. • (eg. investment choice influenced because of personal preference for a specific brand) Organizational Culture Close to the power play: the way we look at how we have to work together in an organisation • Encompasses set of assumptions that define goal and product – What products the organization should produce – How and where it should be produced – For whom the products should be produced • May be powerful unifying force as well as restraint on change • (eg. new CRM system is introduced but there is no “quality” assurance culture for data) A customer relationship management system = convert needs into sales Culture? People at the firm who had to insert data into the system did not have a culture of quality control on the data (person says ‘Antwerpen’ or says ‘Antwerp’) Organizational Environments Evolutions and IT will impact the way we organise our businesses (IoT): it may be that our business strategy requires new technology: technology is often used as a way to look at the environment: environment can influence or business strategy • Organizations and environments have a reciprocal relationship • Organizations are open to, and dependent on, the social and physical environment • Organizations can influence their environments • Environments generally change faster than organizations • Information systems can be instrument of environmental scanning, act as a lens
Disruptive Technologies • Substitute products that perform as well as or better than existing product • Technology that brings sweeping change to businesses, industries, markets • Examples (winner and losers): digital photography, internet music Losers: the people who made tapes for photos/people who made cd’s Winners: new digital camera’s/ Apple • First movers and fast followers – First movers—inventors of disruptive technologies – Fast followers—firms with the size and resources to capitalize on that technology • Note: Garnter Hype Cycle: https://www.youtube.com/watch?v=YDbkY2UoIeo Hype cycle is very popular in the market. It is a way to look at the technology and where they are in the maturity Organizational Structure Structure of the organization will also have an impact on which technology we will use: organizational structure will impact the information system structure • Five basic kinds of organizational structure (Mintzberg) – Entrepreneurial (young, simple structure, eg. start-up) – Machine bureaucracy (bureaucracy, centralized, slow chaning, eg. midsize manufacturing) – Divisionalized bureaucracy (combination of bureaucracies, different products/services, eg. General Motors) – Professional bureaucracy (knowledge based, experts, weak centralized authority, hospital) – Adhocracy (task force oriented, eg. consultancy firm) • Information system often reflects organizational structure Other Organizational Features • Goals – Coercive (prison), utilitarian (business), normative (university), and so on • Constituencies Stakeholders: the more stakeholders are involved the more complicated the information systems are • Leadership styles • Types of tasks Economic impact: Transaction Cost Theory Transaction cost = costst that organziations have to make when they want to require goods and services in the market • Firms seek to economize on transaction costs (the costs of participating in markets) – Vertical integration, hiring more employees, buying suppliers and distributors • IT lowers market transaction costs, making it worthwhile for firms to transact with other firms rather than grow the number of employees (eg. Dell)
Become a vertical integrated company: do everything yourself: you have less transaction costs: you can become a bigger company: IT can lower the transaction cost Because of IT it can become more efficient because IT makes it easier to do transactions in the market IT is reducing the transaction cost = economic impact Economic impact: Agency Theory = owner of the company and the agent that works for the company = costs that you have to make as an owner to control the agent: agent will maybe not work by himself for your best interest à A big company has a lot more agency costs than a small company • Firm is nexus of contracts among self-interested parties requiring supervision • Firms experience agency costs (the cost of managing and supervising) which rise as firm grows • IT can reduce agency costs, making it possible for firms to grow without adding to the costs of supervising, and without adding employees Impact of IT? Agency cost can go down because of the use of technology, systems that give you more information at hand, in real time, makes it for the owner much more efficient to control your workers Force people to work in a specific way trough an information system à Agency cost reduces Organizational and Behavioral Impacts It supports our move towards post – industrial organizations = knowledge central systems Middle management can just be replaced by IT: you will have a flat organizational structure • IT flattens organizations – Decision making is pushed to lower levels – Fewer managers are needed (IT enables faster decision making and increases span of control)
• Postindustrial organizations – Organizations flatten because in postindustrial societies, authority increasingly relies on knowledge and competence rather than formal positions (information systems enable task-force & network oriented organizations in which groups comes together to complete a specific task). – As an example, read p. 120-121 (Can technology replace managers?) Understanding Organizational Resistance to Change Understand the resistance of change: will always be there in organizations Why is there resistance? If you introduce something new in an organization, you also have to change the structure, the people, the job tasks and the information technology • Information systems become bound up in organizational politics because they influence access to a key resource—information • Information systems potentially change an organization’s structure, culture, politics, and work • Four factors – Nature of the innovation – Structure of organization – Culture of organization – Tasks affected by innovation The Internet and Organizations The transaction cost and agency cost have reduced dramatically since the internet was introduced • The Internet increases the accessibility, storage, and distribution of information and knowledge for organizations • The Internet can greatly lower transaction and agency costs – Example: Large firm delivers internal manuals to employees via a corporate website, saving millions of dollars in distribution costs Implications for the Design and Understanding of Information Systems • Organizational factors in planning a new system: – Environment – Structure § Hierarchy, specialization, routines, business processes – Culture and politics – Type of organization and style of leadership – Main interest groups affected by system; attitudes of end users – Tasks, decisions, and business processes the system will assist
Porter’s Competitive Forces Model (!) • Why do some firms become leaders in their industry? • Michael Porter’s competitive forces model – Provides general view of firm, its competitors, and environment • Five competitive forces shape fate of firm: Porter: as an organization you have to look outside: what are the competitive forces out there that can impact your business? – Traditional competitors – New market entrants – Substitute products and services – Customers – Suppliers Figure 3.8: Porter’s Competitive Forces Model Information System Strategies for Dealing with Competitive Forces • Low-cost leadership For example: Colruyt wants to be the cheapest so they use a supply chain management system to make sure they deliver the cheapest – Produce products and services at a lower price than competitors – Example: Walmart’s efficient customer response system • Product differentiation For example: you can buy a fully customized shoe online – Enable new products or services, greatly change customer convenience and experience – Example: Google, Nike, Apple – Mass customization ßà mass production • Focus on market niche Focus only on the customers that are identified as highly profitable (using technology to create unique services) – Use information systems to enable a focused strategy on a single market niche; specialize – Example: Hilton Hotels’ OnQ system • Strengthen customer and supplier intimacy – Use information systems to develop strong ties and loyalty with customers and suppliers – Increase switching costs Cost of switching from one product to a competing product – Examples: Chrysler, Amazon, Starbucks, KLM
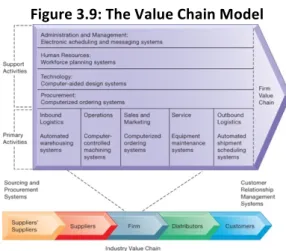
What happened with the bargaining power of the customers of Brussels airlines since the internet? It has become more easy for the customer to compare: chose an airline that has the lowest cost: bargaining power has increased: Brussels airlines suffers from that KLM invested in social media: put your complaint on social media: guarantee that within one hour they will help u out For example: bookstore Competitive force: you have e-books these days (substitute products) New market entrance, if you have a bookshop, the entry barrier to begin a new shop is very low: you can just begin an online bookstore: because of the internet the competitive forces are changing: they are becoming threats: how to change the threats into opportunities? = use technology to create a strategy The Internet’s Impact on Competitive Advantage • Transformation or threat to some industries – Examples: travel agency, printed encyclopedia, media • Competitive forces still at work, but rivalry more intense • Universal standards allow new rivals, entrants to market • New opportunities for building brands and loyal customer bases Smart Products and the Internet of Things • Internet of Things (IoT) – Growing use of Internet-connected sensors in products • Smart products – Fitness equipment, health trackers • Expand product differentiation opportunities – Increasing rivalry between competitors • Raise switching costs • Inhibit new entrants • May decrease power of suppliers The Business Value Chain Model Tries to explain how a company creates value for the customer; always have primary and secondary activities – Firm as series of activities that add value to products or services – Highlights activities where competitive strategies can best be applied • Primary activities vs. support activities – At each stage, determine how information systems can improve operational efficiency and improve customer and supplier intimacy – Utilize benchmarking, industry best practices
Figure 3.9: The Value Chain Model Primary activities can only operate if there are supporting of secondary activities Connection to IT? IT can help us make a specific activity more effective and efficient Extending the Value Chain: The Value Web • Firm’s value chain is linked to value chains of suppliers, distributors, customers • Industry value chain • Value web – Collection of independent firms using highly synchronized IT to coordinate value chains to produce product or service collectively – More customer driven, less linear operation than traditional value chain Figure 3.10: The Value Web Synergies Whole value chain has become digitalised: organizations use software to make those activities more effective and efficient (RP system or many different systems) IT helps us to create synergies • When output of some units are used as inputs to others, or organizations pool markets and expertise • Example: merger of Bank of NY and JPMorgan Chase When two bancs merge: they will merge with the potential of creating synergies: banc has merged and IT is used in the back office to create and put together all those business processes Core competencies IT can be used to create a strength in core competencies • Activity for which firm is world-class leader • Relies on knowledge, experience, and sharing this across business units • Example: Procter & Gamble’s intranet and directory of subject matter experts
Network-Based Strategies • Take advantage of firm’s abilities to network with one another • Include use of: – Network economics – Virtual company model – Business ecosystems Network economics Economic models that do not suffer from decreasing marginal profits: the bigger the network, the bigger the gain for all the members in the network • Marginal cost of adding new participant almost zero, with much greater marginal gain • Value of community grows with size • Value of software grows as installed customer base grows • Compare to traditional economics and law of diminishing returns • Eg. Uber, Airbnb Virtual company model Integrated trough an information system • Virtual company – Uses networks to ally with other companies – Creates and distributes products without being limited by traditional organizational boundaries or physical locations • Example: Li & Fung – Manages production, shipment of garments for major fashion companies – Outsources all work to thousands of suppliers Business Ecosystems and Platforms • Industry sets of firms providing related services and products • Platforms – Microsoft, Facebook • Keystone firms (eg. Apple) They provide a platform • Niche firms (eg. developers of Apps) Thousands of little companies that make apps for the iPhone • Individual firms can consider how IT will help them become profitable niche players in larger ecosystems For example: city banc was the fist banc that used technology to get money out of the wall City bank became the biggest banc of the world because of this technology but the technology has commoditised: first company with this competitive advantage but other players will also embrace this technology IT à Value Start investing in IT more: it is not because we invest in IT that we get the value: research that demonstrates that if you are in a position of alignment (investing in the right context in your business strategy) IT strategy is in line with your business strategy = more value
Challenges Posed by Strategic Information Systems • Sustaining competitive advantage – Competitors can retaliate and copy strategic systems – Systems may become tools for survival • Aligning IT with business objectives – Performing strategic systems analysis § Structure of industry § Firm value chains • Managing strategic transitions – Adopting strategic systems requires changes in business goals, relationships with customers and suppliers, and business processes
Chapter 8: Securing Information Systems
Focus on the risk that we have while using technology in our business processes. Story of Stuxnet: https://www.youtube.com/watch?v=7g0pi4J8auQ The more we are becoming digitalized, the more threats there are: we have to be aware of the risk that emerges out of technology Hackers Attack Singapore’s Telecom Infrastructure • Hackers targeted one of Singapore’s major telecom companies with a massive DDoS attack • Demonstrates vulnerabilities in information technology systems • Illustrates the some of the reasons governments and firms need to pay special attention to information system security Service attack: sending millions of messages to one central server and the central server will shut down then Why Systems Are Vulnerable • Security – CIA • Controls – Methods, policies, and organizational procedures that ensure safety of organization’s assets; accuracy and reliability of its accounting records; and operational adherence to management standards One of the risks that we face is information security, the topic of information security is always defined with the 3 letter word CIA: − Confidentiality of information (only people who are authorized have access to information) − Integrity (is the date accurate?) − Availability (information has to be available at an appropriate time) Management controls are things that you implement in your organization to make sure there are no CIA concerns For example: passwords before you go on blackboard = security control to ensure confidentiality Figure 8.1: Contemporary Security Challenges and Vulnerabilities Where can things go wrong? Everywhere (security concerns) − iPhone can be stolen (= confidentiality breach) − power interruption at home and laptop is ruined (= availability, you have no information) The more we are depending on technology, the more challenges and threats we haveInternet Vulnerabilities – Network open to anyone – Size of Internet means abuses can have wide impact – Use of fixed Internet addresses with cable / DSL modems creates fixed targets for hackers – Unencrypted VOIP (voice over IP) – E-mail, P2P, IM (peer to peer, instant messaging) • Interception • Attachments with malicious software • Transmitting trade secrets Wireless Security challenges − Radio frequency bands easy to scan (à wireless network, even at home) − SSIDs (service set identifiers) Identify access points: broadcast multiple times: can be identified by sniffer programs − War driving Eavesdroppers drive by buildings and try to detect SSID and gain access to network and resources Once access point is breached: the intruder can gain access to networked drives and files − Rogue access points Figure 8.2: Wi-Fi Security Challenges Malicious Software: Viruses, Worms, Trojan Horses, and Spyware Malicious Software: Viruses, Worms, Trojan Horses, and Spyware • Malware (malicious software) Just a broad definition of all types of software that can do bad things with your machine • Viruses (typically spreading after human action) Piece of software that can damage your machine, there needs to be a human action to spread the virus (for example: an e-mail) • Worms (independent) Also a software program, they can independently spread themselves: it makes the impact much more severe • Worms and viruses spread by – Downloads and drive-by downloads – E-mail, IM attachments • Mobile device malware (risk to corporate systems) Locks or reads the pin code that you press into your mobile phone For example: for your banking app • Social network malware (users trust messages) Facebook and Instagram are ‘’trusted’’, virus in a message on Facebook or Instagram • Trojan horse It means that you are receiving something that seems to be friendly/common, but you click on it and you can get a virus
• SQL injection attacks (abuse entry pages on website) If developers of an online form did not secure the form good enough, the ‘’bad’’ guys can encrypt a virus in those rows (database): he or she can get then access to all the information • Ransomware You have been on a website that has been infected, and you get a virus, your laptop will lock down and you get a message with ‘’pay 500$ otherwise we will hack your computer’’ • Spyware – Key loggers Spyware will know when you open up your online banking system and will know when you are asked to give your pin code Hackers and Computer Crime • Hackers vs. crackers Crackers: are the really bad guys, want to get money Hackers: there can be good hackers, hack a company to explain which threats they are facing, not to damage them • Activities include: − System intrusion − System damage − Cyber vandalism Intentional disruption, defacement, destruction of a website or a corporate information system • Spoofing and sniffing Sniffing: online transaction between A and B, sniffing between someone who steals the communication à intercept a message Spoofing: the bad guy pretends to be someone else, for example: a mail that appears to be an e-mail from your bank (bad guy pretends to be a trusted party) For example: go to the website of UA but the server is hacked, webpage looks like UA website but in fact it’s something else: the spoofed website asks your login • Denial-of-service attacks (DoS) All computers are infected (botnet) and they will send messages to the network • Distributed denial-of-service attacks (DDoS) Causes the website to shut down • Botnets • Computer crime − Computer may be target of crime − Computer may be instrument of crime • Identity theft − Phishing (eg. email messages) ‘’Bank’’ that sends you an e-mail that your password has expired, click here to change your password: in this way they will get access to your password − Evil twins You think you are on a Wi-Fi network but you actually are somewhere else (see above) − Pharming (you type in the right URL, but you come on another webpage, infected) You think you are on a website but you actually are somewhere else (see above) • Click fraud The fact that there are many banners on the internet (: company has to pay for the banner), if you click on the link you are directed to the website: par click the company with the banner has to pay: so you can damage the organization to click fraud: the company has to pay a lot • Cyberterrorism • Cyberwarfare
Cause damage and disruption by penetrating its networks and computer + defending yourself Internal Threats: Employees • Security threats often originate inside an organization • Inside knowledge • Sloppy security procedures − User lack of knowledge • Social engineering Is about the fact that ‘’bad’’ guys can easily convey you, you are not aware that they are stealing information Software Vulnerability • Commercial software contains flaws that create security vulnerabilities − Bugs (program code defects) − Zero defects cannot be achieved because complete testing is not possible with large programs − Flaws can open networks to intruders • Patches − Small pieces of software to repair flaws − Exploits often created faster than patches can be released and implemented Our software has security holes: places where it’s not secured Zero day: moment when hackers attack your system, the day the developer is not yet aware of the security hole, how long will it take before the company will see there is a security hole? Main concern is in yourself, we are way to easy to give out of information What Is the Business Value of Security and Control? • Failed computer systems can lead to significant or total loss of business function A failed computer system can have an impact on your business process which has an impact on your business • Firms now are more vulnerable than ever All information is in information systems: we are digitalized organization – Confidential personal and financial data – Trade secrets, new products, strategies • A security breach may cut into a firm’s market value almost immediately Imaging that your organization is noted on the stock exchange: when a city bank has been hacked they can have all your information: people do not trust this bank anymore: the value of the company will implode, there is a lot of damage and the stock will go down • Inadequate security and controls also bring forth issues of liability Legal and Regulatory Requirements for Electronic Records Management More and more digitised environments: new laws and regulations are popping up • HIPAA (Health insurance portability and accountability act) – Medical security and privacy rules and procedures Enforces hospitals and medical organizations to demonstrate that they can ensure your private information: comply with the act of privacy: if they can not demonstrate this they have to pay a fine • Gramm-Leach-Bliley Act – Requires financial institutions to ensure the security and confidentiality of customer data Similar but financial institutions • Sarbanes-Oxley Act
– Imposes responsibility on companies and their management to safeguard the accuracy and integrity of financial information that is used internally and released externally About the accuracy of information: if organizations do not adapt to these regulations, they can not operate Electronic Evidence and Computer Forensics • Electronic evidence – Evidence for white collar crimes often in digital form – Proper control of data can save time and money when responding to legal discovery request • Computer forensics – Scientific collection, examination, authentication, preservation, and analysis of data from computer storage media for use as evidence in court of law – Recovery of ambient data Information Systems Controls • May be automated or manual • General controls − Govern design, security, and use of computer programs and security of data files in general throughout organization’s information technology infrastructure (organizational things you are going to organise that apply to all information system) − Software controls, hardware controls, computer operations controls, data security controls, system development controls, administrative controls, Identity management: who works for my company? When someone is fired, the identity management has to maker sure that they can not get access to information of the company, restrict the access Access management: which person has to get access to which information? • Application controls − Controls unique to each computerized application − Input controls, processing controls, output controls Risk Assessment Determines level of risk for the firm if a specific activity or process is not properly controlled • Types of threat • Probability of occurrence during year • Potential losses, value of threat • Expected annual loss Take this from a risk manager perspective A risk manger is a doom thinker (= think about all the things that can go wrong with the company) for example: risk scenario that the electricity falls out and you have lost all the information on your laptop He identifies the risk scenario − Likelihood: what is the chance that this will happen − When it happens what is the impact? Line called risk appetite (= how much risk are you willing to /or can you take as a business) In terms of risk, CIA are 3 examples of that: if these risk are elevated (beyond your risk appetite) we accept the risk: how are we going to mitigate that? Take measures to make sure that the likelihood decreases or you take measures to make sure that when it happens the impact will be reduced
Example: Security police for protecting the company’s assets • Ranks information risks, identifies acceptable security goals, and identifies mechanisms for achieving these goals • Drives other policies – Acceptable use policy (AUP) § Defines acceptable uses of firm’s information resources and computing equipment • Identity management – Identifying valid users – Controlling access Figure 8.3: Access Rules for a Personnel System Disaster Recovery Planning and Business Continuity Planning When something fails how can we make sure we are up and running as soon as possible: working on the impact: example of general control • Disaster recovery planning – Devises plans for restoration of disrupted services • Business continuity planning – Focuses on restoring business operations after disaster • Both types of plans needed to identify firm’s most critical systems – Business impact analysis to determine impact of an outage – Management must determine which systems restored first The Role of Auditing • Information systems audit – Examines firm’s overall security environment as well as controls governing individual information systems • Security audits – Review technologies, procedures, documentation, training, and personnel – May even simulate disaster to test responses • List and rank control weaknesses and the probability of occurrence • Assess financial and organizational impact of each threat
Manager: understanding risks and implementing the control: auditor will control whether the manager has implement the control Figure 8.4: Sample Auditor’s List of Control Weaknesses What Are the Most Important Tools and Technologies for Safeguarding Information Systems? • Authentication – Password systems – Tokens – Smart cards – Biometric authentication – Two-factor authentication (fingerprint) • Firewall Real walls that organizations build between the internet and the corporation: wall will track all the information that will go in and out the organization – Combination of hardware and software that prevents unauthorized users from accessing private networks – Technologies include: • Packet filtering • Tasteful inspection • Network address translation (NAT) • Application proxy filtering • Intrusion detection system – Monitors hot spots on corporate networks to detect and deter intruders • Antivirus and antispyware software – Checks computers for presence of malware and can often eliminate it as well – Requires continual updating • Unified threat management (UTM) systems Figure 8.5: A Corporate Firewall
Securing Wireless Networks • WEP security – Static encryption keys are relatively easy to crack – Improved if used in conjunction with VPN • WPA2 specification – Replaces WEP with stronger standards – Continually changing, longer encryption keys Encryption and Public Key Infrastructure • Encryption – Transforming text or data into cipher text that cannot be read by unintended recipients (people that sniff your communication • Two methods of encryption – Symmetric key encryption § Sender and receiver use single, shared key – Public key encryption § Uses two, mathematically related keys: public key and private key § Sender encrypts message with recipient’s public key § Recipient decrypts with private key For example: allows secure information exchange between two parties Figure 8.6: Public Key Encryption • Digital certificate – Data file used to establish the identity of users and electronic assets for protection of online transactions – Uses a trusted third party, certification authority (CA), to validate a user's identity – CA verifies user’s identity, stores information in CA server, which generates encrypted digital certificate containing owner ID information and copy of owner’s public key • Public key infrastructure (PKI) – Use of public key cryptography working with certificate authority – Widely used in e-commerce Ensuring System Availability • Online transaction processing requires 100% availability • Fault-tolerant computer systems – Contain redundant hardware, software, and power supply components that create an environment that provides continuous, uninterrupted service • Deep packet inspection (slow networks – give priority to critical traffic- • Security outsourcing (accountability remains)
Security Issues for Cloud Computing and the Mobile Digital Platform • Security in the cloud – Responsibility for security resides with company owning the data – Firms must ensure providers provide adequate protection: § Where data are stored § Meeting corporate requirements, legal privacy laws § Segregation of data from other clients § Audits and security certifications – Service level agreements (SLAs) • Securing mobile platforms – Security policies should include and cover any special requirements for mobile devices § Guidelines for use of platforms and applications – Mobile device management tools § Authorization § Inventory records § Control updates § Lock down/erase lost devices § Encryption – Software for segregating corporate data on devices Ensuring Software Quality • Software metrics: Objective assessments of system in form of quantified measurements – Number of transactions – Online response time – Payroll checks printed per hour – Known bugs per hundred lines of code • Early and regular testing • Walkthrough: Review of specification or design document by small group of qualified people • Debugging: Process by which errors are eliminated
Chapter 9: Achieving operational excellence and customer intimacy: enterprise
applications
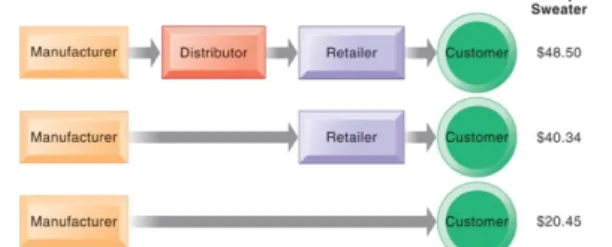
Key system applications for the digital age: deep dive in how can technology improve/innovate in each of these business domains? (marketing, production) Alimentation Couche-Tard (Convenience store) Competes Using Enterprise Systems • Problem – Antiquated IT infrastructure and ERP system – disparate processes for each country and market – massive operational inefficiencies • Solutions – Numerous separate legacy systems replaced with Oracle’s JD Edwards Enterprise One ERP system • Demonstrates use of technology to maximize supply chain efficiency, integrate data into a common source Figure 9.1: How Enterprise Systems Work ERP-systems: what is it about? ERP-systems can be highly beneficial in increasing the operational excellence in a company - ERP system always builds on a central data base (allows for integration) - Allows for standardization: ERP-system will build generic business processes in software: looking at many organizations trying to understand how typically a marketing and sales (HR, finance…) process is organized: all these views on a business process have been summarized in a best practices view, they are automated and implemented in the software à allows for integration and standardization Enterprise Software • Built around thousands of predefined business processes that reflect best practices – Finance and accounting – Human resources – Manufacturing and production – Sales and marketing • To implement, firms should – Select functions of system they wish to use If you are in an organization that decides to implement SAP: automate and integrate all of the business processes/whole value chain: as a company, you can buy the whole ERP system (introduce everything of your business in SAP) (all these business processes in an integrated ERP system) or you can only buy the HR functionalities from SAP – Map business processes to software processes § Use software’s configuration tables for customizingThe way I organize my marketing and sales process is not the same as in SAP: organization wants to customize SAP à Risk (standardization = comply with the best practice other wise the whole business case will not fly) Business Value of Enterprise Systems • Increase operational efficiency • Provide firm-wide information to support decision making Integration: one central database: easy to connect and report management information • Enable rapid responses to customer requests for information or products • Include analytical tools to evaluate overall organizational performance • Example: https://www.youtube.com/watch?v=OUwh6knoL10 (P&G) Log in for marketing and sales in system A, finance in system B: different systems with different databases: confusing and ineffective One global company: all business process into one integrated application: easy access to all data: standardized approach: all share the same business platform à work an integrated and standardized approach across the globe The supply chain • Network of organizations and processes for: – Procuring materials, transforming them into products, and distributing the products Network of organizations: how goods flow in a network of organizations from production to consumers • Upstream supply chain – Firm’s suppliers, suppliers’ suppliers, processes for managing relationships with them • Downstream supply chain – Organizations and processes responsible for delivering products to customers • Internal supply chain Figure 9.2: Nike’s Supply Chain Supply chain has 2 parts: down stream supply chain: make shoes à distributer à retailer Up stream supply chain: supplier à supplier à supplier Supply Chain Management • Importance of timely and accurate information Supply chain where all the elements in the supply chain will keep stock: costly business: we have to make our supply chain efficient: timely and accurate is important – Inefficiencies cut into a company’s operating costs § Can waste up to 25 percent of operating expenses – Just-in-time strategy
– Safety stock: Buffer for lack of flexibility in supply chain If organizations are at huge uncertainty they will keep safety stock: very expensive – Bullwhip effect § Information about product demand gets distorted as it passes from one entity to next across supply chain Happens in the supply chain when information is not communicated in the right phase in the supply chain à the bullwhip effect Figure 9.3: The Bullwhip Effect Local retailer makes a short time promotion campaign for milk: as a result of the short time promotion campaign the demand will go up: if it’s not communicated in the supply chain that this was a one time, all the other players in the supply chain might increase their stock: they are preparing for the next time it happens: is a huge waste: it is not happening so we have to see that the information in the supply chain is timely and accurate: information systems will help to ensure better flows of information in the suplpy chain Supply Chain Management Software • Supply chain planning systems – Model existing supply chain – Enable demand planning (calculate how much product a business needs to satisfy customer demand) Help organization to calculate how much products a business requires: saves us costs – Establish inventory levels – Identify transportation modes Make sure that products will be delivered in time, at the right place in the supply chain • Supply chain execution systems – Manage flow of products through distribution centers and warehouses (delivering products to the right locations in the most efficient manner) • Complexity increases in global supply chains – Example: https://www.youtube.com/watch?v=KWABT48wTFw 175 000 small spare parts distributed around the globe at the appropriate time: They use software to make the traject more efficient